Technology can be unstable, confusing, and ever-changing.
It’s frustrating when you think you’ve figured it out, only for hackers to find a way around your security measures.
You install a patch to fix a software vulnerability, but then another patch is needed to fix the vulnerabilities created by the previous patch.
It’s a constant arms race with no end in sight.
That’s why more and more businesses are turning to managed services providers for their IT needs.
These providers proactively manage your networks, inside and out.
They have a team of professionals who get to know your IT structure inside and out.
They fix problems before they affect your bottom line and offer suggestions to optimize processes, saving you time, money, and headaches.
It’s like having your own IT department without the hassle of hiring and training employees.
Managed services providers take care of everything, so you can focus on running your business. They keep up with the latest technology trends and ensure your systems are always up-to-date and secure.
So why stress about technology when you can have experts take care of it for you?
With managed services, you can stay relevant and competitive in today’s fast-paced world.
Leave the tech stuff to the professionals and enjoy the peace of mind of knowing your IT is in good hands.

That’s not all:
- In just one year, nearly 1 billion emails were exposed, impacting a staggering 1 in 5 internet users.
That’s a massive amount of sensitive information at risk. And the consequences can be costly.
- In the year 2022, the average cost of a data breach reached an unprecedented peak of $4.35 million, experiencing a notable increase of 2.6% compared to the previous year’s average cost of $4.24 million. That’s a significant hit to their bottom line.
But it’s not just data breaches that are causing havoc in the digital world. Ransomware attacks have been on the rise as well.
In the year 2021, the global count of ransomware attacks reached 623.3 million incidents. That’s a mind-boggling number of attempts to hold data hostage for financial gain.
Without further adieu, let’s take a look at some of the deadliest IT security mistakes and what you need to avoid and data protection.
6 IT security Mistakes: What You Can Avoid It
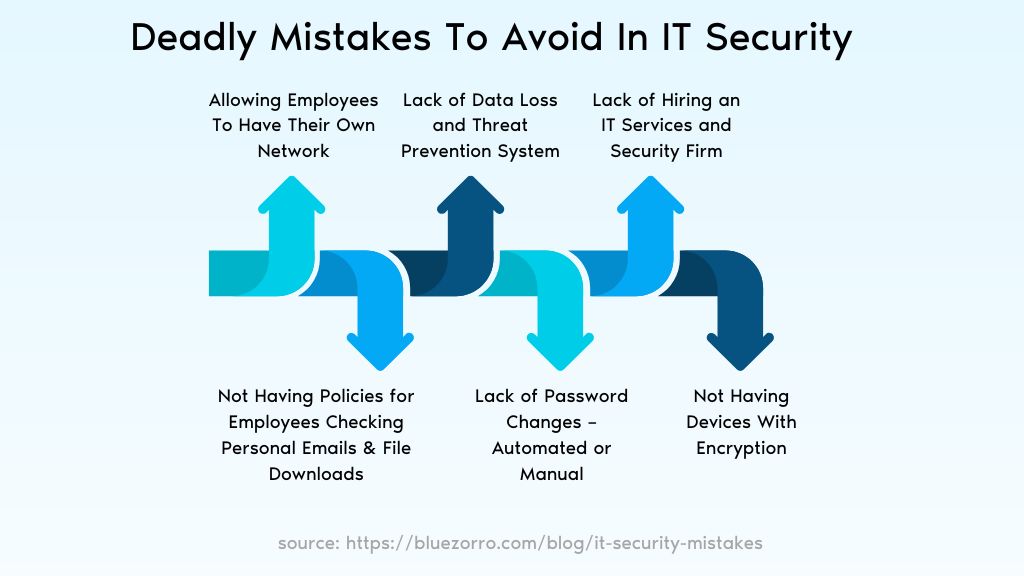
1. Allowing Employees To Have Their Own Network
Nowadays, with computing becoming more spread out and decentralized, it’s a real challenge to keep machines and data secure.
Companies have the freedom to hire the best employees, regardless of where they live.
However, this also means that there are more devices that can be infected with malware.
And if those devices are connected to the company’s network, that malware can infiltrate and steal valuable data.
But it’s not just malware that poses a threat.
Mobile devices are also vulnerable to data leaks.
They can easily be lost or stolen, and outsiders can easily access them. And when data goes missing, it can lead to all sorts of problems – financially, legally, and reputation-wise.
So, what can you do to prevent all of these issues?
1.1 Create A Secure Connection To The Company’s Network
Well, one thing you can do is create a secure connection to the company network and only use that network. This will help reduce the risk of malware infection.
1.2. Use Security Software
Another important step is to use security software and keep your computer updated.
Make sure you’re using the latest versions of all applications and install any new security patches immediately.
Don’t rely on your employees to take care of this – activate automatic updates from software makers or use a patch-management tool to distribute updates yourself.
1.3. Install Encryption Software
And lastly, consider installing encryption software.
This is a great way to protect your data and minimize potential damage if a breach does occur.
So, take these steps seriously and ensure the security of your network and data.
2. Not Having Policies for Employees Checking Personal Emails & File Downloads
Employees need to understand their roles and responsibilities in protecting sensitive data and company resources.
Without this understanding, even the best security technology won’t be helpful.
So, it’s important to establish practices and policies that promote security and provide training to help employees identify and avoid risks.
2.1. Information Security Awareness Training
It’s crucial for your company’s security strategy that employees are properly trained on it. Information security awareness training is of utmost importance.
You must ensure that employees are aware of how and when it’s safe to share information.
This knowledge will help them make informed decisions regarding data sharing.
2.2. Provide Specific Education To Employees About Different Threats
To create an effective security awareness program, it’s essential to educate employees about various threat types.
Some examples of these threats include malware, trojans, viruses, social engineering, and phishing.
By providing specific education on these threats, employees will be better equipped to recognize and handle potential risks.
2.3. Continuous Training And Reinforcement
Remember that cybersecurity is not a one-time effort. It requires continuous training and reinforcement.
Make sure to regularly update your security awareness program to address new types of threats and evolving techniques used by malicious actors.
By investing in employee training and creating a culture of security awareness, you can significantly enhance your company’s overall security posture.
This will help protect sensitive data, safeguard company resources, and mitigate the risks associated with cyber threats.
3. Lack of Password Changes – Automated or Manual
Automated password changes may seem like a minor thing, but they are actually quite important.
You see, password cracking is surprisingly easy for advanced hackers. So by taking this small step of changing your password regularly, you can protect your firm’s sensitive information.
Did you know that it takes an average of 16 months for companies to even notice a security breach? During that time, hackers are stealing sensitive data that can never be retrieved.
Here’s how it works in the real world.
Many usernames are simply the person’s email address.
According to a study conducted by Spycloud in 2021, approximately 70 percent of individuals tend to reuse passwords for their personal accounts.
Interestingly, even Fortune 500 employees are not exempt from this habit, as the study reveals that 64 percent of them use the same password on multiple accounts.
So if one site gets hacked, your credentials are out there for the taking.
And with a little social engineering, those bad actors can gain access to your banking, retail, retirement, medical, and other sites that hold valuable data.
This is exactly why they want your social media passwords too.
By getting into your social media accounts, they can gather information about you that can be used to unlock even more valuable data.
So it’s a good idea to require your employees to change their passwords regularly.
Make sure their passwords are long and strong, with a mix of uppercase and lowercase letters, numbers, and symbols.
And don’t forget to keep those passwords private.
It should all be a part of your company’s policy to keep everyone’s information safe.
4. Lack of Data Loss and Threat Prevention System
Not having a data loss prevention system in place can put sensitive information at risk in today’s digital world.
It’s no longer enough to just lock up physical file cabinets.
4.1. Email Vulnerabilities
Your email data is stored on your device in “files” that can be accessed and read by various programs, which can even display attachments.
Malware often targets email, making it a common method for stealing information.
An analysis of 81 million messages sent over 27 years reveals that only a mere 0.06 percent of emails are encrypted.
When training new employees, it’s crucial to give clear instructions on what should and should not be sent via email.
They need to understand the importance of protecting sensitive data and the potential consequences of not doing so.
4.2. Free Rein To Sensitive Information
In addition to email vulnerabilities, there are numerous applications like Dropbox, Google One Drive, and Box that allow data to be sent from a network and stored in personal accounts.
This means that employees could be making copies of company data and storing it offsite without the business owner’s knowledge. It’s like giving free rein to sensitive information, thousands of times a day.
To prevent these risks, it’s essential for companies to implement some form of Data Loss Prevention (DLP) system.
This will help protect sensitive data from falling into the wrong hands and ensure that proper security measures are in place.
It’s a necessary step in today’s digital landscape to safeguard against data breaches and maintain the trust of customers and clients.
5. Not Having Devices With Encryption

Data theft is a real problem for businesses nowadays.
Laptops get stolen, cloud storage accounts get hacked, employees steal important files, and USB drives get lost. And the consequences can be serious.
Losing a laptop or phone means losing critical information like trade secrets, app codes, or financial records. It can set you back a lot of time and effort.
According to PC World Magazine, there are 82,000 new malware viruses created every day.
This means that the threats are constantly growing and spreading. To protect yourself, you need multiple layers of security.
So, what can you do?
The best solution is to encrypt all your devices.
From your old desktop to your brand new Windows system, and even your employees’ smartphones, all need to be protected.
Encryption converts your data into a code that is unreadable to anyone without the decryption key.
This way, even if your device gets lost or stolen, your data remains secure.
Implementing encryption might take some time and effort, but it’s worth it. It gives you peace of mind knowing that your sensitive information is safe.
So, don’t wait until it’s too late. Take action now and protect your business from data theft.
6. Lack of Hiring an IT Services and Security Firm
Not hiring an IT security services firm can lead to several potential downsides and risks for an organization:
6.1. Increased Vulnerability to Cyber Attacks
Without expert IT security services, an organization may have inadequate protection against cyber threats.
Cybercriminals continuously evolve their tactics, and without proactive monitoring and defense measures, the organization’s data and systems could be at higher risk of being compromised.
6.2. Lack of Expertise and Experience
IT security services firms are staffed with cybersecurity experts who possess specialized knowledge and experience in dealing with a wide range of security challenges.
Without their expertise, an organization may struggle to identify and address security vulnerabilities effectively.
6.3. Limited Resources for Incident Response
In the event of a security breach, an IT security services firm can rapidly respond to contain and mitigate the impact of the incident.
Without this external support, an organization might struggle to manage the incident effectively, leading to prolonged downtime, data loss, and reputational damage.
6.4. Compliance and Regulatory Issues
Many industries have specific data security and privacy regulations that organizations must adhere to.
IT security services firms can assist in ensuring compliance with these regulations.
Failure to comply can result in legal and financial consequences.
6.5. Higher Cost of Recovery
Dealing with a cybersecurity incident after it occurs can be significantly more expensive than investing in proactive security measures.
Data recovery, legal fees, reputational damage repair, and potential fines can create a substantial financial burden.
6.6. Difficulty in Implementing Best Practices
IT security services firms can implement industry best practices and standards to protect an organization’s data and infrastructure.
Without this guidance, an organization may struggle to adopt the most effective security measures.
6.7. Inability to Keep Pace with Technology
IT security is a rapidly evolving field. New threats and vulnerabilities emerge regularly, and security technologies continuously advance.
Without an IT security services firm, an organization may fall behind in adopting the latest security measures.
6.8. Internal Bias and Blind Spots
In-house IT teams may have inherent biases or blind spots when evaluating their organization’s security posture.
An external IT security services firm can provide an objective and unbiased assessment of the organization’s security strengths and weaknesses.
6.9. Underestimation of Risk
Some organizations may underestimate the risks associated with cyber threats, assuming they won’t be a target.
However, cybercriminals target organizations of all sizes, making it essential to prioritize security regardless of perceived risk.
6.10. Limited 24/7 Monitoring and Support
Many IT security services firms offer round-the-clock monitoring and support. Without such services, an organization’s security may be more vulnerable during non-business hours.
Discover a World of Secure and Smooth IT with Blue Zorro

Your Trusted IT Partner
Welcome to Blue Zorro, where we believe in empowering businesses like yours to navigate the digital realm with confidence and ease.
We understand the challenges and complexities you face in managing your IT infrastructure while safeguarding it against cyber threats.
That’s why we are here – to be your trusted IT partner, providing unparalleled managed IT services and expert IT security consultancy solutions.
Unparalleled Managed IT Services
At Blue Zorro, we take pride in offering top-notch managed IT services that cater to the unique needs of businesses, no matter the size or industry.
From startups to large enterprises, our team of dedicated professionals is equipped with the knowledge and experience needed to ensure your IT environment runs smoothly and efficiently.
Let us take care of the technical complexities while you focus on growing your business and serving your customers.
A Partnership That Makes a Difference
At Blue Zorro, we don’t just offer generic solutions; we strive to build strong partnerships with our clients.
We take the time to understand your unique challenges and objectives, enabling us to tailor our services accordingly.
Our personalized touch ensures that you feel valued and supported every step of the way.
When you partner with us, you gain a dedicated team that is invested in your success.
Unlocking Your Business Potential
In conclusion, Blue Zorro is your gateway to a world of secure and smooth IT operations.
Our top-notch managed IT services and specialized IT security consultancy solutions will empower your business to scale, grow, and thrive in the digital era.
With us by your side, you can confidently leverage technology as a catalyst for innovation and success.
Don’t let IT challenges hold you back; get in touch with Blue Zorro today and embark on a journey toward a secure and prosperous future. Together, we can conquer the digital landscape!
Feel free to get in touch with us today.


