Protecting your business and client data from cyberattacks is a big responsibility.
These attacks can happen to any industry or company, but smaller businesses are often the easiest targets because they lack proper security measures.
In this blog, we’ll share some important facts about cybersecurity and provide tips on how to keep your data safe.
Understanding Cybercrimes

First, let’s define cybercrime.
Cybercrime refers to criminal activities carried out through digital means and the internet.
It involves the use of computers, networks, and electronic devices to commit illegal acts or harm individuals, organizations, or governments.
Cybercriminals exploit vulnerabilities in computer systems and online environments to gain unauthorized access, steal sensitive information, disrupt services, commit financial fraud, spread malware or viruses, engage in identity theft, engage in online harassment, and perpetrate various other illicit activities.
Common forms of cybercrime include hacking, phishing, ransomware attacks, identity theft, online scams, cyberbullying, distributed denial-of-service (DDoS) attacks, and data breaches.
Cybercrime poses significant threats to individuals, businesses, and societies, leading to financial losses, compromised privacy, reputational damage, and disruptions in various sectors.
Here are a few key facts you should know about cybersecurity:
- A company falls victim to a ransomware attack every 11 seconds, on average. This alarming statistic emphasizes the urgency of implementing strong security measures.
- Human error is responsible for 95% of data breaches. This highlights the importance of educating employees about cybersecurity best practices to minimize the risk of mistakes.
- UK companies are incurring an average cost of £3.4 million due to data breaches. This staggering figure underscores the financial impact of a breach.
- A whopping 22 billion records were exposed in data breaches in 2021. This highlights the scale of the problem and the need for robust security measures.
- In 2020, the number of malware cases increased by 358% compared to the previous year, while ransomware attacks saw a 435% increase. These alarming statistics indicate the growing threat of cyberattacks.
Given these facts, it’s crucial for businesses of all sizes to prioritize cybersecurity. Implementing effective security measures, training employees, and staying informed about the latest threats are key steps in safeguarding your data.
6 Tips for Data and Document Safety In 2023
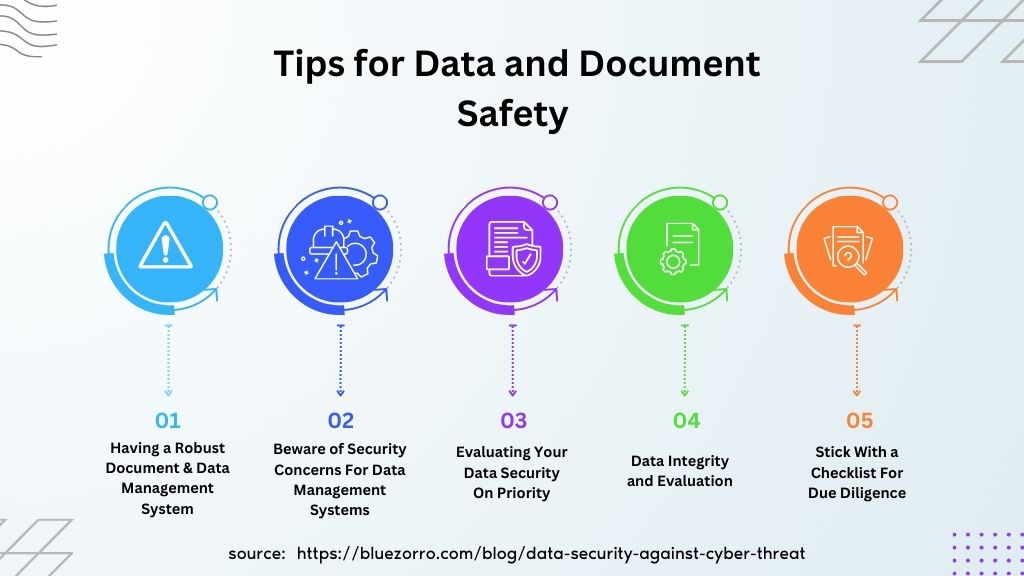
1. Having a Robust Document & Data Management System
So, what exactly is a Document Management System (DMS) and why do you even need it?
Well, in simple terms, a DMS is software that helps businesses collect and manage their information digitally.
It does a bunch of cool things like automating processes such as collecting, protecting, archiving, digitizing, categorizing, approving, and managing business files.
So, how does this benefit your business?
1.1. Saves Time
Well, by digitizing all your documentation and paperwork, a document management system allows your business to focus on what it’s actually supposed to be doing.
No more wasting time searching through piles of paper or dealing with misplaced files. Everything is organized and easy to find.
1.2. Keeps Track
But that’s not all! A DMS also keeps track of all the activity surrounding your files. It logs everything, from when a file enters the system to when it leaves.
This ensures that you have a clear and detailed record of all the actions taken on your documents.
1.3. Ensures Security
And let’s not forget about security. A document management system offers a secure cloud-based backup.
This means that all your important files are stored in a safe and accessible place.
No need to worry about lost or damaged files. Plus, it’s a cost-effective solution that scales with your business.
With all these benefits, it’s no wonder that more and more businesses are turning to a DMS for their digital needs.
It’s a centralized and secure system that not only improves efficiency but also addresses cybersecurity concerns.
So, if you want to streamline your business processes and keep your files organized and secure, a document management system is definitely worth considering.
It’s time to free your business from the shackles of paperwork and embrace the digital age.
2. Beware of Security Concerns For Data Management Systems

When considering a document management platform, it’s crucial to address the security concerns surrounding the information stored within it.
Let’s take a closer look at the most common concerns.
2.1. Physical Security Aspect
First off, we have the physical security aspect.
This refers to the protection of the physical servers and data centers where your data is stored.
Ensuring that these locations have sufficient security measures in place is essential.
2.2. Operational Security
Next, we have operational security. This encompasses access control, workflow approvals, and audit conformance.
It’s important to know who has access to what information and what permissions they possess in terms of viewing, suggesting, commenting, and editing.
Clearly defining and managing these data privileges is key.
2.3. Encryption Technologies
Encryption technologies play a vital role as well.
You’ll want to ensure that the platform utilizes up-to-date encryption methods to safeguard your data from unauthorized access.
Monitoring and notification systems are essential for promptly identifying and addressing any system incidents that may occur.
Being able to flag and generate detailed reports on these issues is crucial for maintaining the security of your documents.
2.4. Vulnerability Testing Of Web Applications
Additionally, conducting vulnerability testing of web applications and remote access to document tools is important.
Regularly assessing the system’s vulnerability to potential threats is necessary for its overall security.
2.5. Backups
Lastly, backups are a critical aspect of document management.
Understanding the backup policy employed by the platform and evaluating its robustness is vital.
You want to be confident that your data is being adequately backed up to prevent any loss.
Taking these security concerns into account will help ensure that your chosen document management platform adequately protects your organization’s valuable information.
3. Evaluating Your Data Security On Priority
Data security is important.
No one wants to deal with data loss or litigation, especially when it can result in fines and damage to a business’s reputation.
To assess the security of your documents and information, ask yourself these questions:
- How do we protect against internal security breaches?
- Are we safeguarded against hacking threats?
- What’s our plan for accessing and recovering data after a natural disaster?
- Could we be accused of mismanaging data?
- Can we demonstrate proper handling of documents and data? Do we have a clear retention policy for sensitive information?
- Are there any financial penalties we could face?
To further understand how documents are handled, consider how employees engage with them.
Ask yourself:
- Can employees access the documents they need quickly?
- Do they always have the most up-to-date versions?
- Are employees trained in proper document handling and protection against social hacking?
Once you have the answers to these questions, you’ll know which document security features are most important for your organization.
4. Data Integrity and Evaluation
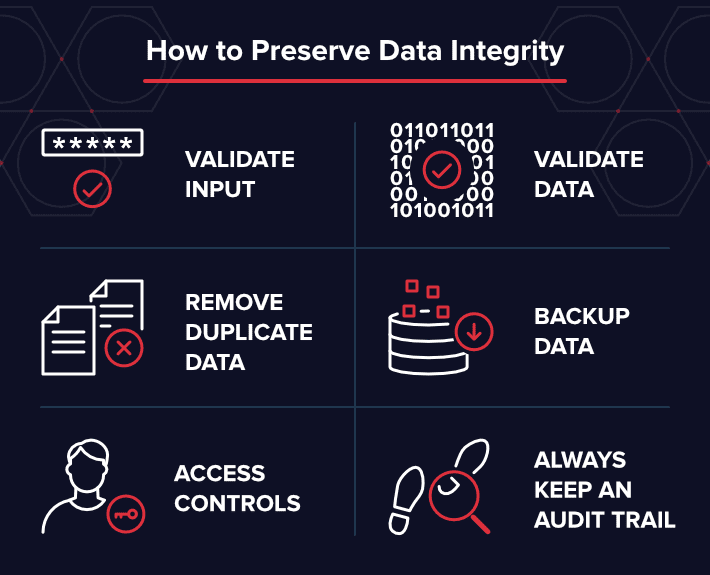
It’s important for you and your business to have trust in the authenticity of every document, every time it’s accessed.
Encryption and access rights are meaningless unless you can validate the state and authenticity of each document.
A document management system ensures this by implementing a few key features.
4.1 Electronic Signatures
First, electronic signatures provide the most secure form of digital signature.
These qualified electronic signatures guarantee that the signature is legitimate and that the document hasn’t been tampered with.
This is because an authorized Trust Service Provider authenticates the signer and issues a digital certificate for validation.
4.3. Version Management
Next, version management plays a crucial role in maintaining document validity.
When a document is accessed and changes are made, the system should check out and check in the document.
This creates a new version, preserving the history of changes and recording who made them and when.
It ensures that users only update and edit the most current version of the document.
4.3. Change Logs
Lastly, change logs are essential for tracking the entire history of a document.
Every access, annotation, and workflow state should be recorded in the system.
This allows for the reconstruction of the document’s history if needed.
You should be able to access this information through a CSV file or other common file format.
By implementing these features, a document management system enables you to trust the authenticity of your documents and have confidence in their integrity.
5. Stick With a Checklist For Due Diligence
When you’re considering getting a document management system for your organization, there’s a lot to think about.
5.1. System’s Security
One important aspect is the system’s security.
You’ll want to make sure it has strong authentication measures, like individual user logins.
It should also allow you to control who has access to what information, whether that’s specific individuals, groups, or even certain data within documents.
5.2. Data Backup
Another thing to consider is data backup.
You’ll want a system that not only backs up your data but also stores it in separate geographical locations for added security.
In terms of encryption, look for a system that uses 256-bit encryption to protect your sensitive information.
5.3. Workflow And Retention Policies
Workflow and retention policies are also important features to look for.
These will help you streamline your document processes and ensure that documents are retained or disposed of according to your organization’s policies.
5.4. Complain Requirements
Compliance requirements are another consideration.
Make sure the system you choose meets any industry or regulatory standards that your organization needs to adhere to.
Document integrity is crucial as well.
You’ll want a system that allows you to validate the integrity of your documents to ensure that they haven’t been tampered with or altered in any way.
5.5. Integration With Other Business Applications
Integration with other lines of business applications, like ERPs or CRMs, should also be a consideration.
You’ll want to make sure that the system can securely integrate with these applications to streamline your workflows.
5.6. Accountability And Tracking
In terms of logging, it’s important to choose a system that logs every change made to a document.
This will help with accountability and tracking.
5.7. System’s Uptime And Availability
Finally, consider the system’s uptime and availability.
You’ll want a system that ensures maximum uptime, so you can access your documents whenever you need them.
Overall, when evaluating a document management system’s security, it’s important to ask these questions and find a system that meets your organization’s specific needs.
6. Strong Passwords Vs General Awareness
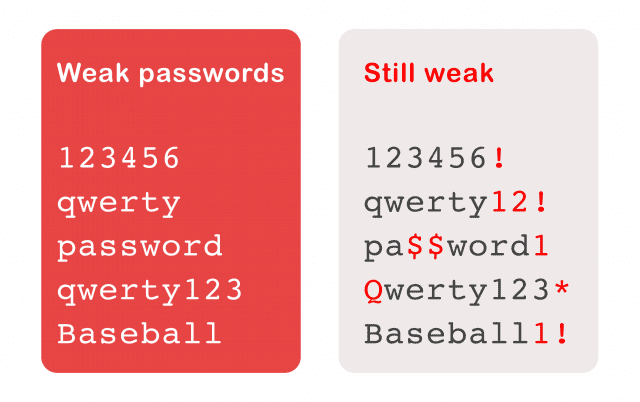
Make sure your passwords are strong on all your devices and accounts where personal information is stored.
Don’t make them easy to guess.
The National Cyber Security Centre recommends using three random words.
6.1. Multi-Factor Authentication
Consider using multi-factor authentication if possible.
This is a security measure to make sure only the right person can access your data.
You need at least two different forms of identification before access is granted.
For example, you might use a password and a one-time code sent by text message. This adds an extra layer of protection to your accounts.
6.2. Be Aware Of Your Surroundings
Also, be aware of your surroundings when using your devices.
For instance, if you’re on a train or in a shared workspace, others may be able to see what’s on your screen.
To prevent this, you can use a privacy screen that limits the visibility of your screen to those directly in front of it.
By following these steps, you can enhance the security of your personal information and reduce the risk of unauthorized access to your accounts.
Stay vigilant and take the necessary precautions to protect your privacy and data.
General Trends And Attributes To Keep In Mind
Other than that, here are some general trends and attributes of cybersecurity that you need to keep in mind.
1. Increased Adoption of Zero Trust Architecture
Zero Trust is an approach to cybersecurity that requires verifying every user and device trying to access a network or resource, regardless of whether they are inside or outside the corporate perimeter.
This principle is gaining popularity as organizations aim to enhance their security posture and protect sensitive data from unauthorized access.
2. Blockchain for Document Authentication
Blockchain technology can provide a tamper-proof and decentralized way to validate the authenticity and integrity of documents.
By using blockchain, individuals, and businesses can ensure the legitimacy of contracts, certificates, and other critical documents.
3. Biometric Authentication

As biometric technology becomes more sophisticated and prevalent, it may play a more significant role in data security.
Biometric authentication, such as fingerprint, facial, or iris recognition, can offer a higher level of security compared to traditional passwords or PINs.
4. AI and Machine Learning in Threat Detection
Artificial intelligence (AI) and machine learning (ML) are already being employed to detect and respond to cybersecurity threats in real time.
These technologies can help organizations stay ahead of emerging threats and better protect their data and documents.
5. Privacy-Preserving Technologies
With increasing concerns over data privacy, there is a growing focus on privacy-preserving technologies.
Techniques like homomorphic encryption, secure multi-party computation, and differential privacy allow data to be processed and analyzed without compromising individual privacy.
6. Cloud Security Enhancements
As more data and documents are stored in the cloud, cloud security will continue to evolve.
Expect more robust encryption methods, improved access controls, and compliance features to safeguard data stored in cloud environments.
7. Cybersecurity Regulations and Compliance
Governments and industries worldwide are expected to strengthen data protection laws and regulations.
Organizations will need to comply with these regulations and invest in security measures to protect sensitive information adequately.
8. Quantum Computing Threats and Solutions
Quantum computing has the potential to break conventional encryption algorithms, posing a threat to data security.
Consequently, the development of post-quantum cryptography (encryption methods resistant to quantum attacks) will gain importance.
9. Internet of Things (IoT) Security
As IoT devices continue to proliferate, securing these interconnected devices and the data they generate will be critical.
The challenge lies in maintaining security across a wide range of devices with varying levels of computing power and capabilities.
10. User Education and Awareness
Despite advanced security technologies, human error remains a significant factor in data breaches.
Therefore, there will be a continued emphasis on educating users about best practices for data security, including how to handle documents securely.
Over To You
Technology is a constantly evolving landscape with disruptive growth prospects.
One best way to ensure data security is to hire an IT services and consultancy firm, such as Blue Zorro.
Besides offering managed IT solutions, the company has a team of professionals capable of advising on data compliance and security strategies to help secure your business from a long-term safety perspective.
Unleash the Power of Custom Software Solutions with BlueZorro!

Are you tired of one-size-fits-all software that just doesn’t cut it for your business? Look no further!
At BlueZorro, we offer cutting-edge custom software development services that are tailor-made to meet your unique requirements and propel your success.
Why Choose BlueZorro for Your Software Development Needs?
Expertise You Can Trust
Our team of industry insiders comprises seasoned professionals who possess the knowledge and experience to cater to your every need and surpass your expectations.
With BlueZorro, you’re in the hands of experts who understand the intricacies of your industry.
Stand Out from the Crowd
Say goodbye to generic solutions!
Our custom software development services are designed to make your business stand out in the crowd.
We craft solutions that are personalized to match your specific goals, helping you achieve a competitive edge in the market.
Partner with the Best
BlueZorro is your ideal technology partner, dedicated to taking your business to new heights through innovative and customized software solutions.
One best way to ensure data security is to hire an IT services and consultancy firm, such as Blue Zorro.
Join Our Esteemed Clientele
Trust the names that trust us! These industry leaders have experienced the power of BlueZorro’s custom software development, and now it’s your turn to take advantage of our expertise.
Don’t settle for mediocrity.
Elevate your business with our exceptional software development services.
Partner with BlueZorro today and witness the difference!


